In our computer age, humanity is increasingly refusing to store information in handwritten or printed form, preferring electronic documents for this . And if earlier they simply stole paper or parchments, now electronic information is hacked. The data encryption algorithms themselves have been known since time immemorial. Many civilizations preferred to encrypt their unique knowledge, so that only a knowledgeable person could get it. But let's see how all this is displayed on our world.
What is a data encryption system?
First you need to decide what cryptographic systems are in general. Roughly speaking, this is a special algorithm for recording information that would be understood only by a certain circle of people.
In this sense, to an outsider everything that he sees should (and, in principle, it is) seem like a meaningless set of characters. Only one who knows the rules for their location can read this sequence. As the simplest example, you can define an encryption algorithm with writing words, say, backwards. Of course, this is the most primitive that you can think of. It is understood that if you know the rules of recording, it will not be difficult to restore the original text.
Why is this needed?
Why all this was thought up, probably, it is not worth explaining. Look, after all, what volumes of knowledge left from ancient civilizations are today in encrypted form. Either the ancients did not want us to find out, or all this was done so that a person could use them only when he reaches the desired level of development - so far, one can only speculate about this.
However, if we talk about today's world, information security is becoming one of the biggest problems. Judge for yourselves, because there are so many documents in the same archives that some governments would not want to distribute, how many secret developments, how many new technologies. But all this, by and large, is the primary goal of the so-called hackers in the classical sense of the term.
Only one phrase that has become a classic of the principles of Nathan Rothschild’s activity comes to mind: “Whoever owns the information owns the world.” And that is why information has to be protected from prying eyes, so that it is not used by someone else for their own selfish purposes.
Cryptography: reference point
Now, before considering the very structure that any encryption algorithm has, we will plunge a little into history, in those distant times when this science was only in its infancy.

It is believed that the art of data hiding actively began to develop several millennia ago BC. Championship is attributed to the ancient Sumerians, King Solomon and the Egyptian priests. Only much later appeared the same runic signs and symbols similar to them. But what’s interesting: sometimes the encryption algorithm of the texts (and they were encrypted at that time) was such that in the same ancient Sumerian cuneiform writing one character could mean not only one letter, but also a whole word, concept or even sentence. Because of this, the decryption of such texts even in the presence of modern cryptographic systems, allowing to restore the original form of any text, becomes absolutely impossible. Speaking in modern language, these are quite advanced, as it is now commonly expressed, symmetric encryption algorithms. We will dwell on them separately.
The modern world: types of encryption algorithms
As for the protection of confidential data in the modern world, it is worthwhile to dwell separately on those times when computers were unknown to humanity. Not to mention how much paper the alchemists or the same Templars translated trying to hide the true texts about the knowledge they knew, it is worth remembering that since the connection arose, the problem has only worsened.
And here, perhaps, the most famous device can be called a German cryptographic machine of the Second World War under the name "Enigma", which is translated from English as "mystery". Again, this is an example of how symmetric encryption algorithms are used, the essence of which is that the encryptor and decryptor know the key (algorithm) originally used to hide data.
Today, such cryptosystems are used everywhere. The most striking example is, say, the AES256 encryption algorithm, which is an international standard. In terms of computer terminology, it allows the use of a 256-bit key. In general, modern encryption algorithms are quite diverse, and they can be conditionally divided into two large classes: symmetric and asymmetric. They, depending on the area of destination, are used today very widely. And the choice of encryption algorithm directly depends on the tasks and the method of restoring information in its original form. But what is the difference between the two?
Symmetric and asymmetric encryption algorithms: what is the difference
Now let's see what a cardinal difference between such systems is, and on what principles their application in practice is based. As already clear, encryption algorithms are associated with geometric concepts of symmetry and asymmetry. What this means will now be clarified.
The symmetric DES encryption algorithm, developed back in 1977, implies the presence of a single key, which, presumably, is known to two interested parties. Knowing such a key, it is not difficult to put it into practice in order to read the same meaningless set of characters, bringing it, so to speak, in a readable form.
And what are asymmetric encryption algorithms? Two keys are used here, that is, for encoding the source information, it uses one, for decrypting the content - the other, and it is absolutely not necessary that they coincide or are simultaneously located at the encoding and decoding side. For each of them, one is enough. Thus, in a very high degree, both keys are prevented from falling into third hands. However, based on the current situation, theft of this type is not a particular problem for many attackers. Another thing is the search for exactly that key (roughly speaking, a password) that is suitable for decrypting data. And here there may be so many options that even the most modern computer will process them for several decades. As stated, not a single computer system in the world can crack access to it and get what is called “wiretapping”, and cannot and will not be able in the next decades.
The most famous and commonly used encryption algorithms
But back to the computer world. What are the main encryption algorithms designed to protect information at the present stage of development of computer and mobile technology?
In most countries, the de facto standard is the 128-bit key AES cryptographic system. However, in parallel with it , the RSA encryption algorithm is sometimes used , which, although it relates to encryption using a public (public) key, is nevertheless one of the most reliable. This, by the way, has been proved by all leading experts, since the system itself is determined not only by the degree of data encryption, but also by maintaining the integrity of the information. As for the early developments, which include the DES encryption algorithm, it is hopelessly outdated, and attempts to replace it began in 1997. It was then based on it that a new Advanced encryption standard AES appeared (first with a key of 128 bits, then with a key of 256 bits).
RSA Encryption
Now let's focus on RSA technology, which refers to an asymmetric encryption system. Suppose one subscriber sends another information encrypted using this algorithm.
For encryption, two sufficiently large numbers X and Y are taken, after which their product Z, called the module, is calculated. Next, a certain extraneous number A is selected that satisfies the condition: 1 <A <(X - 1) * (Y - 1). It must be simple, that is, do not have common divisors with the product (X - 1) * (Y - 1) equal to Z. Then the number B is calculated, but only so that (A * B - 1) is divided by ( X - 1) * (Y - 1). In this example, A is the public key, B is the private key, (Z; A) is the public key, (Z; B) is the private key.
What happens when shipping? The sender creates an encrypted text, designated as F, with the initial message M, followed by raising to the power of A and multiplying by the module Z: F = M ** A * (mod Z). The receiver needs to calculate a simple example: M = F ** B * (mod Z). Roughly speaking, all these actions come down exclusively to exponentiation. By the same principle, the option of creating a digital signature also works, but the equations here are somewhat more complicated. In order not to clog the user with algebra, such material will not be given.
As for hacking, the RSA encryption algorithm poses an intractable task for the attacker: to calculate the key B. This could theoretically be done using available factoring tools (factorization of the original numbers X and Y), but today there are no such tools, therefore, the task itself becomes not only difficult - it is generally impossible.
DES encryption
We have yet another, in the past, quite effective encryption algorithm with a maximum block length of 64 bits (symbol), of which only 56 are significant. As mentioned above, this technique has already become outdated, although it has survived for a long time as a standard for the cryptosystems used in USA even for the defense industry.
The essence of its symmetric encryption is that it uses a certain sequence of 48 bits. At the same time, 16 cycles from a selection of keys of 48 bits are used for operations. But! All cycles according to the principle of action are similar, therefore, at the moment, it is not difficult to calculate the desired key. For example, one of the most powerful computers in the United States, worth more than a million dollars, breaks encryption for about three and a half hours. For machines of a lower rank, no more than 20 hours are required to calculate even the sequence in its maximum manifestation.
AES Encryption
Finally, we have before us the most widespread and, as was thought until recently, invulnerable system - the AES encryption algorithm. It is presented today in three versions - AES128, AES192 and AES256. The first option is used more to ensure the information security of mobile devices, the second is involved at a higher level. As a standard, this system was officially introduced in 2002, and its support was immediately announced by Intel, which manufactures processor chips.
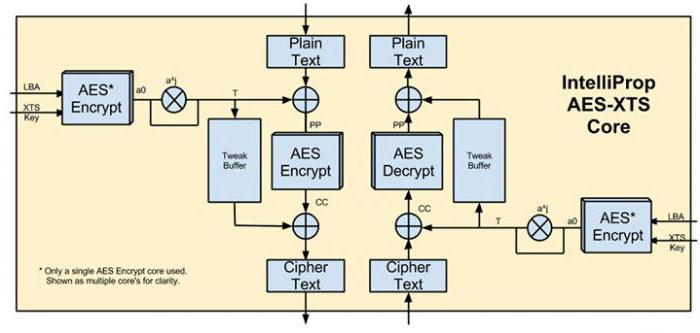
Its essence, unlike any other symmetric encryption system, is reduced to calculations based on the polynomial representation of codes and calculation operations with two-dimensional arrays. According to the United States government, it would take about 149 trillion years to crack a 128-bit key, even the most modern one. Let us disagree with such a competent source. Computer technology over the past hundred years has made a leap commensurate with geometric progression, so it’s not worth it to flatter yourself, especially since today, as it turned out, there are encryption systems and better than those that the United States has declared completely crack-resistant.
Problems with viruses and decryption
Of course, we are talking about viruses. Recently, quite specific ransomware viruses have appeared that encrypt all the contents of the hard drive and logical partitions on the infected computer, after which the victim receives a letter notifying that all the files are encrypted, and only the specified source can decrypt them after paying a tidy sum.
At the same time, what is most important, it is indicated that the AES1024 system was used for data encryption, that is, the key length is four times the current AES256, and the number of options when searching for the corresponding decoder increases incredibly.
And if we proceed from the statement of the US government on the time allotted for decrypting a 128-bit key, then what about the time it takes to find a solution for the case with the key and its variants with a length of 1024 bits? It was then that the United States and pierced. After all, they believed that their computer cryptography system was perfect. Alas, there were some specialists (apparently, in the post-Soviet space) who surpassed the "unshakable" American postulates in all respects.
With all this, even the leading developers of antivirus software, including Kaspersky Lab, the specialists who created Doctor Web, ESET Corporation and many other world leaders simply shrug their hands, they say, there’s simply no means to decrypt such an algorithm, silent about that there’s not enough time. Of course, when contacting the support service, it is proposed to send the encrypted file and, if any, preferably its original - in the form in which it was before encryption. Alas, even a comparative analysis has not yet produced tangible results.
The world we do not know
What can I say if we are chasing the future, not being able to decipher the past. If you look at the world of our millennium, you can see that the same Roman emperor Gaius Julius Caesar used symmetric encryption algorithms in some of his messages. Well, if you look at Leonardo da Vinci, it all becomes somehow uncomfortable from the mere realization that in the field of cryptography this person, whose life is covered in a certain fleur of mystery, has surpassed his modernity for centuries.

Until now, many have been haunted by the so-called "Mona Lisa Gonda", in which there is something so attractive that modern people are not able to understand. By the way, some symbols were relatively recently found in the picture (in the eye, on the dress, etc.), which clearly indicate that all this contains some kind of information encrypted by the great genius, which today, alas, we will extract unable. But we did not even mention all sorts of large-scale constructions that could turn over the understanding of the physics of that time.
Of course, some minds are inclined solely to the fact that in most cases the so-called “golden section” was used, however, it does not provide a key to all that huge repository of knowledge, which, as it is believed, is either incomprehensible or lost forever. Apparently, cryptographers still have to do an incredible amount of work to understand that modern encryption algorithms sometimes can not be compared with the achievements of ancient civilizations. In addition, if today there are generally accepted principles of information protection, then those that were used in antiquity, unfortunately, are completely inaccessible and incomprehensible to us.
One more thing. There is a tacit opinion that most of the ancient texts cannot be translated only because the keys to deciphering them are carefully protected by secret societies like Masons, Illuminati, etc. Even the Templars left their mark here. What can we say that the Vatican library remains completely inaccessible to this day? Are the main keys to understanding antiquity stored there? Many experts are inclined to this version, believing that the Vatican deliberately withholds this information from society. So whether it is or not, no one knows yet. But one thing can be said for sure - the ancient cryptography systems were in no way inferior (or perhaps superior) to those used in the modern computer world.
Instead of an afterword
In the end, it is worth saying that not all aspects related to the current cryptographic systems and techniques that they use were considered here. The fact is that in most cases it would be necessary to give complex mathematical formulas and represent calculations, from which most users would simply go around spinning. Just look at an example with a description of the RSA algorithm to figure out that everything else will look much more complicated.
The main thing here is to understand and understand, so to speak, the essence of the issue. Well, if we talk about what are modern systems that offer to store confidential information in such a way that it is available to a limited circle of users, here the choice is small. Despite the presence of many cryptographic systems, the same RSA and DES algorithms clearly lose to the specifics of AES. However, most modern applications designed for completely different operating systems use AES (of course, depending on the application and device). But the “unauthorized" evolution of this cryptosystem, to put it mildly, shocked many, especially its creators. But in general, based on what is available today, it will not be difficult for many users to understand what cryptographic data encryption systems are, why they are needed and how they work.