Despite the fact that the code was repeatedly processed, it was first described by Giovan Battista Bellazo in 1553. Subsequently, he received the name of the French diplomat Blaise Vigenère. This option is simple enough for implementation and understanding, since it is the most affordable method of cryptanalysis.
Method Description
The Wigner cipher includes a sequence of several Caesar ciphers. The latter is characterized by a shift of several lines. For encryption purposes, you can use the table of alphabets, which is called the Vigenere square. In professional circles, it is called as tabula recta. The Vigenere table consists of several rows of 26 characters. Each new line moves to a certain number of positions. As a result, the table contains 26 different Caesar fonts. Each stage of encryption involves the use of a different alphabet, which is selected depending on the symbol of the keyword.
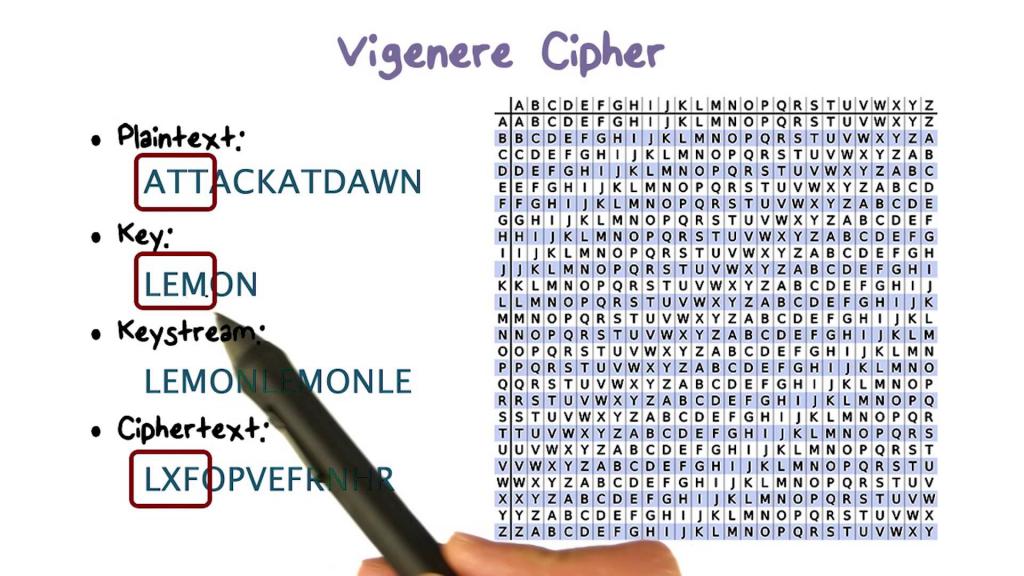
In order to better understand the essence of this method, consider text encryption using the word ATTACKATDAWN as an example. The person who sends the text records the keyword “LEMON” until it matches the length of the transmitted text. The keyword will be LEMONLEMONLE. The first character of the given text - A - is encrypted with the sequence L, which is the first character of the key. This character is located at the intersection of row L and column A. For the next character of the specified text, the second character of the key is used. Therefore, the second character of the encoded text will look like X. It turned out as a result of the intersection of row E and column T. Other parts of the given text are encrypted in the same way. The result is the word LXFOPVEFRNHR.
Decryption process
The word is decrypted using the Vigenere table. Find the line that matches the first character of the keyword. The string will contain the first character of the ciphertext.
The column that contains this character will correspond to the first character of the source text. Subsequent values will be decrypted in the same way.
Important Tips
Providing ciphertext, you must specify a keyword. It will be needed in order to decrypt the code using the Russian Vizhener cipher as well. In order to make sure the encoding is correct, it is better to double-check the text. If the text is incorrectly encoded, it cannot be decrypted correctly.
When using a Vigenère square with spaces and punctuation, the decryption process will become much more complicated. It is important to know that frequent repetition of a code word will make it easier to decrypt the text. Therefore, the code information should be long.
Method Warning
Vizhener's cipher, like many others, is not reliable, since it is easy to crack. If there is a need to transfer classified information, you do not need to resort to using this method. Other methods have been developed for such purposes. Vigenenera cipher is one of the oldest and most popular encryption methods.
The key is a special phrase. It is repeated several times and written over encrypted text. As a result, each letter of the sent message is shifted relative to the specified text by a certain number, which is specified by the letter of the key phrase. For several centuries, this method has steadily occupied the position of the most reliable encryption method. In the 19th century, the first attempts to break the Vizhener cipher were noted, which were based on determining the length of the key phrase. If its length is known, then the text can be divided into certain fragments, which are encoded by the same shift.
Additional decryption methods
You can expand the original message using the frequency analysis method if the specified text is long enough. The key to cipher comes down to finding the length of the key phrase. There are two main methods that allow you to determine the length of a key phrase. The first method of decoding Vigenere cipher was developed by Friedrich Kasitsky. The basis of this method is the search for bigrams. Its essence lies in the fact that if the same bigram is repeated in the encoded message at a distance that is a multiple of the length of the key phrase, then there is a high probability that it will occur at the same positions in the encrypted text. If you find a given distance, get its divisors, you can get a set of certain numbers. They will be the length of the key phrase. However, this method requires some luck. In large encoded text, random bigrams can be found, which will greatly complicate the decryption process.

The second method for decoding the text was proposed by Friedman. Its essence lies in the cyclic shift of the encoded message. The resulting text is recorded under the original encrypted text and the number of matching letters in the bottom and top line is calculated. The resulting numbers allow you to calculate the so-called index of matches. It is determined by the ratio of matches to the total length of the message. The coincidence index for Russian texts is approximately 6%. However, for random texts, this index is approximately 3 or 1/32. The Friedman method is based on this fact. The encoded text is written with a shift of 1,2,3, etc. positions. Then, for each shift, it is necessary to calculate the index of matches. Thus, it is necessary to make a cyclic shift of the entire message. When the index is shifted by a certain number of characters, its length can increase dramatically. This suggests that the length of the keyword can be equated to a certain number. If a situation occurs in which all the characters are shifted to the same position, the match index will have the same value as the source text. If the index is calculated for the Vigenere cipher, in any case, a comparison of actually random text occurs.
Frequency analysis
If the result of the decryption process is positive, you can enter text in columns. Columns are formed on the basis of the source text. Kasitsky invented the most advanced form of text. However, the means of this method cannot be used if the lattice leaves the standard sequence of letters in the alphabet. Therefore, this method allows you to know the length of the keys only in special cases.